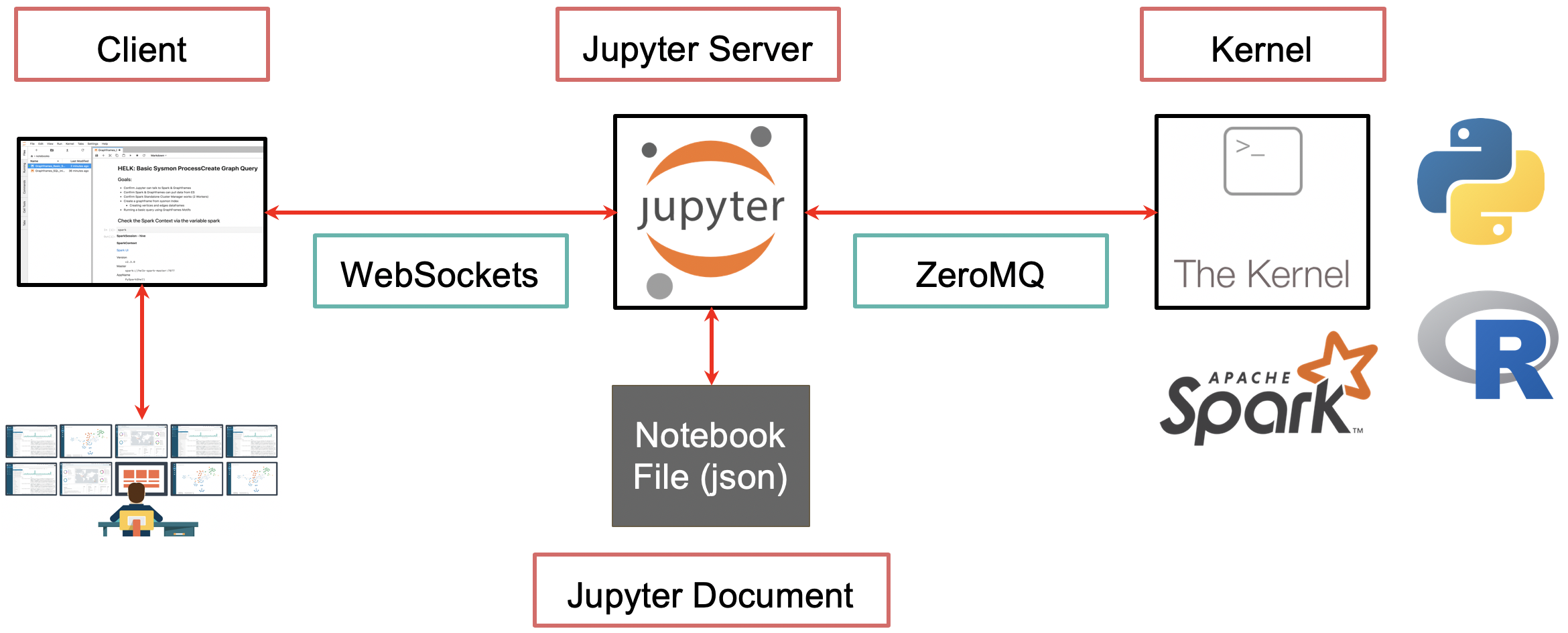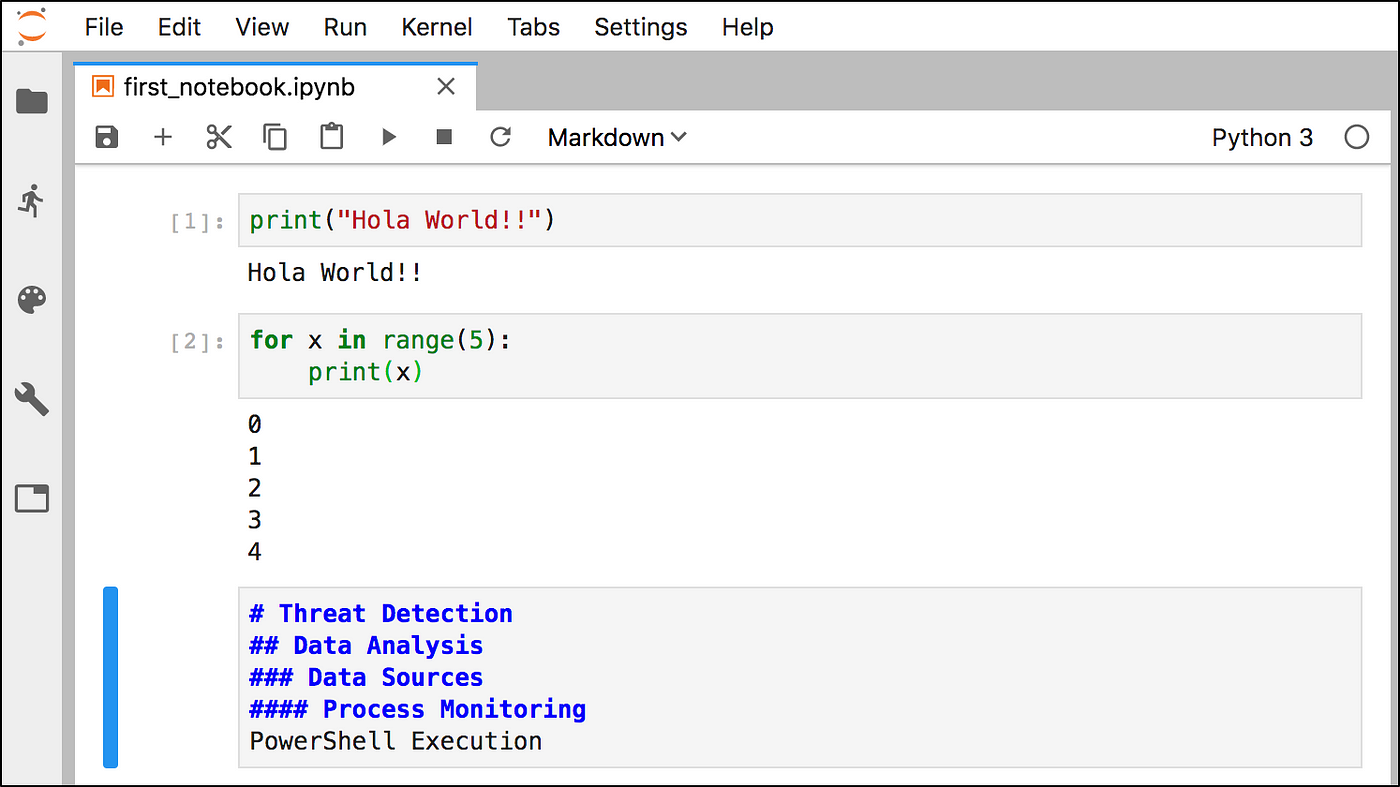
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members

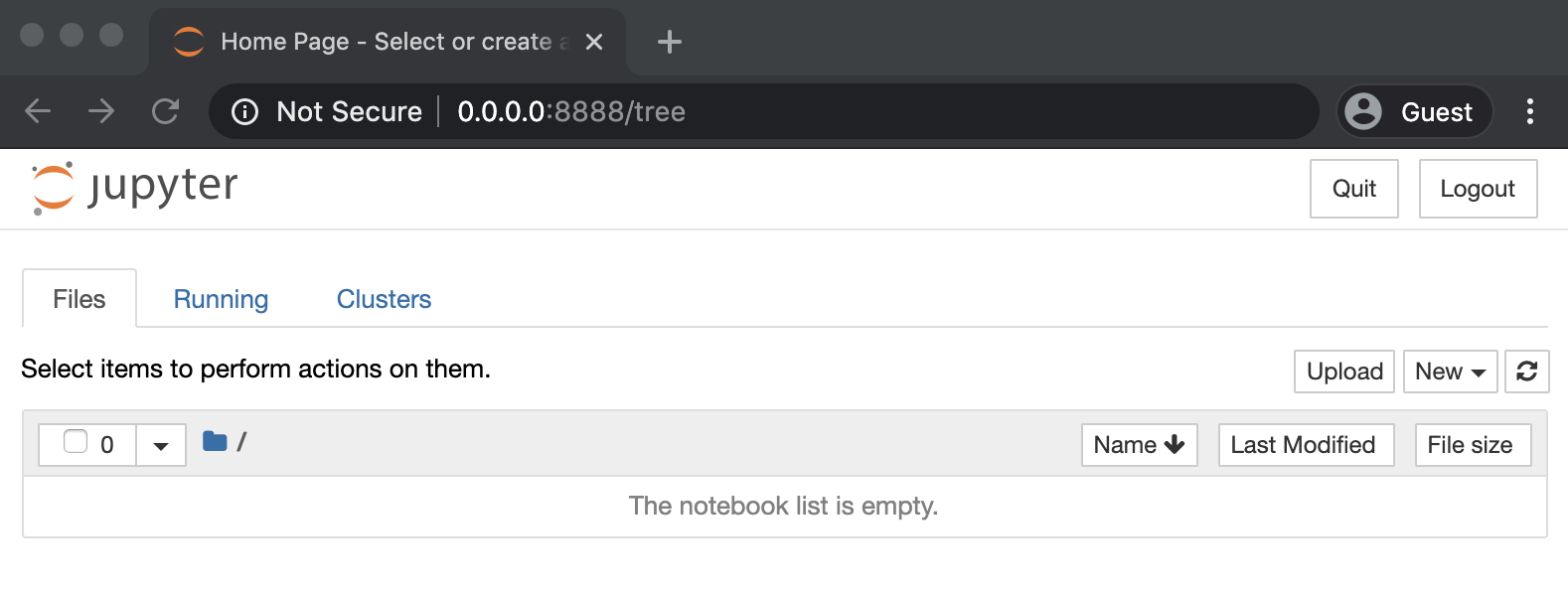
Not able to load the Jupyter notebook UI page Getting Error "EvalError" - JupyterHub - Jupyter Community Forum

Using Jupyter Notebook to analyze and visualize Azure Sentinel Analytics and Hunting Queries – Azure Aggregator

Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members

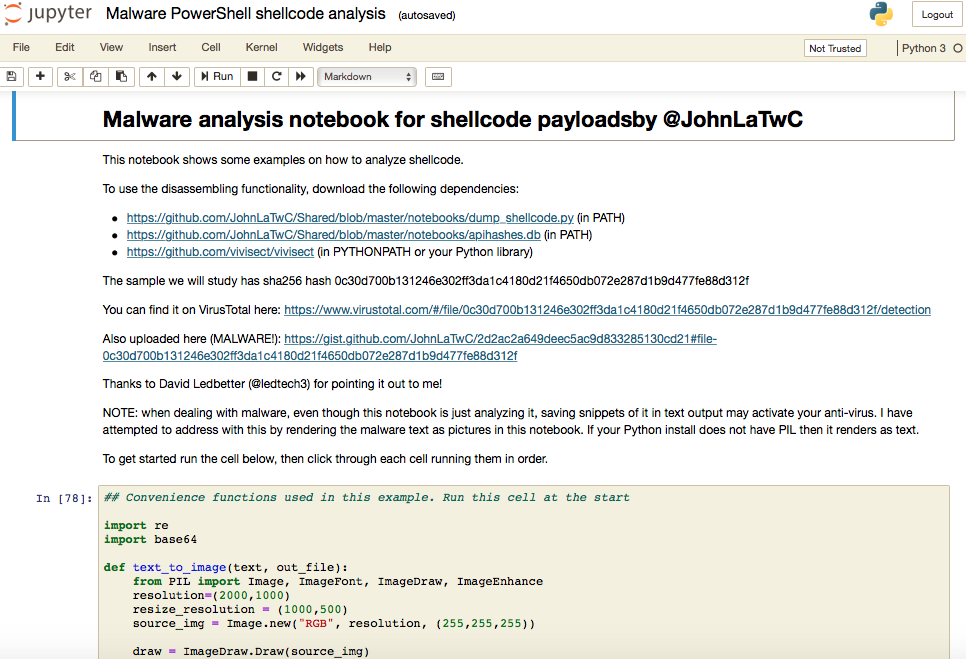
Qubitstrike - An Emerging Malware Campaign Targeting Jupyter Notebooks - Cado Security | Cloud Forensics & Incident Response